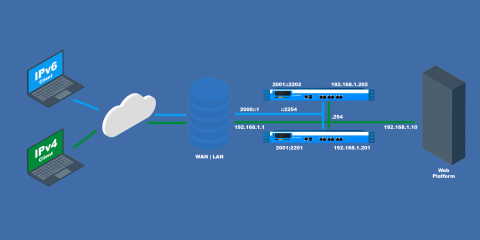
February 2026 — CVE-2026-26080 and CVE-2026-26081: QUIC denial of service
HAProxy patch for two high-severity QUIC vulnerabilities (CVE-2026-26080, CVE-2026-26081) that allow a remote denial of service attack. Upgrade now for protection or disable the QUIC component.









































































































































![Using HAProxy as an API Gateway, Part 6 [Security]](https://cdn.haproxy.com/img/containers/partner_integrations/api-gateway-security.png/809caaf409b9cbba5f53d22b31c00307/api-gateway-security.png)
![Using HAProxy as an API Gateway, Part 5 [Monetization]](https://cdn.haproxy.com/img/containers/partner_integrations/api-gateway-monetization.png/f6ba7bc74399bb3dbeaec96f2813c2f7/api-gateway-monetization.png)
![Using HAProxy as an API gateway, part 4 [metrics]](https://cdn.haproxy.com/img/containers/partner_integrations/api-gateway-4-metrics.png/bead5c0427ca39dcc7c44ed61225e630/api-gateway-4-metrics.png)


















































![Using HAProxy as an API gateway, part 3 [health checks]](https://cdn.haproxy.com/img/containers/partner_integrations/image2-2-%281%29.png/5ef4ef148b968f89804293c3d44312e7/image2-2-%281%29.png)


![Using HAProxy as an API Gateway, Part 2 [Authentication]](https://cdn.haproxy.com/img/containers/partner_integrations/image2-e1548174430466.png/3942e9fa498bb46e325ba72db6f9bd84/image2-e1548174430466.png)






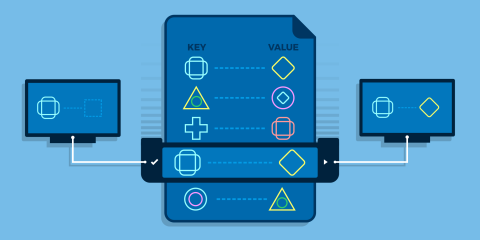

![Using HAProxy as an API gateway, part 1 [introduction]](https://cdn.haproxy.com/img/containers/partner_integrations/2022/api-gateway-pt1/avalanche-area-1080x540.png/2b915c11c726470bf6e314e194c3a7ed/avalanche-area-1080x540.png)