Load balancing VMware Horizon's UDP and TCP traffic: a guide with HAProxy
Learn how to load balance VMware Horizon's complex UDP and TCP traffic using HAProxy's stateless stickiness. Improve remote desktop performance and reliability.

Learn how to load balance VMware Horizon's complex UDP and TCP traffic using HAProxy's stateless stickiness. Improve remote desktop performance and reliability.

Securing traffic between systems is critical. Follow along as we explain how to use SPIFFE and SPIRE to automatically generate and renew identities that include mTLS certificates.

HAProxy Enterprise now supports RADIUS load balancing with the new HAProxy Enterprise UDP Module. We'll outline the challenges with implementing RADIUS load balancing and how to solve them.

AI crawlers from large language model (LLM) companies often ignore the contents of robots.txt and crawl your site. If blocking AI crawlers is your goal, HAProxy Enterprise is the answer. Here's how.

The introduction of ChatGPT caused sharply increased interest in large language models (LLMs). These AI apps also have unique deliverability concerns. Here's how an HAProxy AI gateway can help.

In this post, we will show how you can use an HAProxy Enterprise load balancer to protect against CitrixBleed by placing it in front of your NetScaler instance(s).

We show you how to implement rate limiting based on the ID of the Virtual Private Cloud in Amazon Web Services using HAProxy Enterprise.

In this guide, we’ll explain why connection data matters. Next, we'll cover how the PROXY protocol works, how to use the TShark analyzer to capture and inspect packets and view the extraction results.

Modern load balancers need broad internet protocol support. We’ll outline HAProxy's product-specific protocol support, highlight core features, and share handy use cases.

In this blog post, we show how to collect HTTP header logs and store them remotely to avoid overwhelming your standard log system.

Deeper mailer customization has arrived in HAProxy 2.8! Learn how Lua-based mailers improve on their C-based predecessors and support powerful new monitoring capabilities.

Improvements in acme.sh integration allows you to manage TLS certificates with Let’s Encrypt without restarting HAProxy.

In this article, we’ll take you on a quick tour of the new Lua event framework shipped with HAProxy 2.8—plus demonstrate how Lua helps you further customize HAProxy’s behavior.

In this blog post, you’ll learn how the Proxy Protocol preserves a client’s IP address when that client’s connection passes through a proxy.

In this blog post, you will learn how HAProxy supports sticky sessions. You can choose to implement them either with a cookie or with the user’s IP address.

In this blog post, you’ll learn about several metrics that stand out as particularly useful for monitoring the health of your applications when they’re load balanced by HAProxy.

HAProxy provides three types of health checks: active health checks, passive health checks and agent health checks. In this blog, we will learn about each one.

Learned how to fine tune your HAProxy Kubernetes Ingress Controller’s configuration to leverage powerful annotations to protect your services and APIs.

Learn how to safely test and validate your HAProxy config file with a single command.

In this post, you will learn how to install the open-source edition of HAProxy on Ubuntu, one of the most popular and powerful operating systems around.

Learn how to run HAProxy in a Docker container with this step-by-step guide. Covers configuration, performance considerations, security, and provides ready-to-use commands.

In this blog post, you will learn how to enable service discovery for AWS EC2 instances using HAProxy and the HAProxy Data Plane API.

Learn to configure a basic HAProxy load balancer from scratch. Our tutorial walks you through setting up frontends, backends, and simple routing rules.

In this blog post, you'll learn how to run our Kubernetes Ingress Controller externally to your Kubernetes cluster, which obviates the need for running another load balancer in front.

In this blog, you will learn how to integrate HAProxy and Consul by using the HAProxy Data Plane API, which enables dynamic load balancer configuration changes.

In this blog post, we’ll walk through all of the steps necessary to get your HAProxy metrics displayed in InfluxDB.

Choosing HAProxy as the proxy technology in your Consul service mesh means you’re running a high-performance solution and reducing latency between services.

In this blog post, we’ll see how placing your servers behind HAProxy and using it as an API gateway lets you narrow the point of entry for attackers.
![Using HAProxy as an API Gateway, Part 6 [Security]](https://cdn.haproxy.com/img/containers/partner_integrations/api-gateway-security.png/809caaf409b9cbba5f53d22b31c00307/api-gateway-security.png)
In this post, you will learn how to leverage tokens to grant some users more access than others and then charge for the service. It's called API monetization.
![Using HAProxy as an API Gateway, Part 5 [Monetization]](https://cdn.haproxy.com/img/containers/partner_integrations/api-gateway-monetization.png/f6ba7bc74399bb3dbeaec96f2813c2f7/api-gateway-monetization.png)
In this blog post, you'll learn about the metrics which HAProxy compiles, how to extract them with Prometheus, and visualize them with Grafana or Kibana.
![Using HAProxy as an API gateway, part 4 [metrics]](https://cdn.haproxy.com/img/containers/partner_integrations/api-gateway-4-metrics.png/bead5c0427ca39dcc7c44ed61225e630/api-gateway-4-metrics.png)
In this blog post, we will show several ways of handling multi-domain configurations, including an introduction to using HAProxy maps.

In this blog post, we show how you can use HAProxy connection limits and queues to protect your servers when load balancing heavy amounts of traffic.

In this blog post, you'll learn how to implement a circuit breaker with HAProxy in a simple and more complex way, that allows greater customization.
In this blog post, you will learn several ways to configure HAProxy for proxying SSH, all of which rely on the ssh command's ProxyCommand field.

Learn how to set up HAProxy's cache feature, which will improve how fast you can deliver messages and lessen the load placed upon your backend servers.

HTTP Strict Transport Security (HSTS) sends a user to the secure version of a site without an HTTP redirect. Learn how to enable HSTS with HAProxy.

Read on to learn how to use the HAProxy load balancer to redirect users from HTTP to HTTPS automatically in a few easy steps.

This blog post covers how to set up custom error pages in HAProxy in order to ensure consistent, branded messaging that supports any backend web stack.

Learn how to use the dynamic SSL certificate storage introduced in HAProxy 2.1 and expanded in HAProxy 2.2 in order to update SSL certificates dynamically.

In this blog post, you will learn how to use HAProxy's Deny, Tarpit, Silent Drop, Reject, and Shadowban response policies to stop threats and malicious users.

Learn how to configure TLS with the HAProxy Kubernetes Ingress Controller to provide secure communication to everyone accessing your Kubernetes services.
This blog post shows how to quickly and easily enable SSL/TLS encryption for your applications by using high-performance SSL termination in HAProxy.

HAProxy offers a patch set for enabling seamless reloads of HAProxy without dropping packets in the process. In this blog post, we show you how to enable this.

HAProxy Technologies is proud to announce the availability of an integrated Let’s Encrypt ACMEv2 Lua client for HAProxy and HAProxy Enterprise (HAPEE).

The HTTP 408 status code is an error returned by the server when it doesn't receive a timely request from the client.

Here comes the transparent proxy mode: HAProxy can be configured to spoof the client IP address when establishing the TCP connection to the server.

In this blog post, we show how you can enable inserting client certificate information in HTTP headers and reporting them in the log line with HAProxy.

A brute force attack in WordPress consists of massively sending requests to a URL with different parameters each time. Here's how to prevent it using HAProxy...

In this blog post, we describe how you configure HAProxy to log URLs exactly the way they were sent by the client by using syslog-ng's flexible configuration.

In this blog, we share how to build a high-available RTMP platform for delivering video content with HAProxy and crtmpserver.

HAProxy can support SSL offloading. Today, I’ll focus on how to install and configure HAProxy to offload SSL processing from your servers.

In this blog post, we will provide a configuration that you can use to protect your applications against HTTP request flood attacks.

Geolocation is the process of linking a third party to a geographical location. In easier words: know the country of a client's IP address. On the Internet, such a base is called GeoIP.

In this blog post, we will explain how to configure the HAProxy load balancer to build an efficient SMTP relay infrastructure with Postfix.

In this blog post, we aim to demonstrate how to preserve source IP addresses when using the reverse-proxy mode in HAProxy.

In this blog post, we show how to enable enhanced SSL load balancing with the Server Name Indication (SNI) TLS Extension in HAProxy and HAProxy ALOHA.

In this blog post we will demonstrate how you can send users to the same server for imap and smtp by using HAProxy ALOHA.

Your application uses both HTTP and HTTPS, depending on the pages. SSL encryption is achieved by your backend server directly. Here's how.

Slowloris is a script which opens TCP connections and sends HTTP headers very slowly to force web servers to keep connections opened. The purpose is to...

HAProxy ALOHA allows you to maintain HTTPS sessions based on SSL connection ID. In this blog post, we show you how to configure HAProxy ALOHA for this.

In this blog post we demonstrate how to protect any application or web server against unexpected high load using HAProxy ALOHA.

Build a scalable architecture for a news website using these components: A load balancer with content switching capability, cache server and application server.

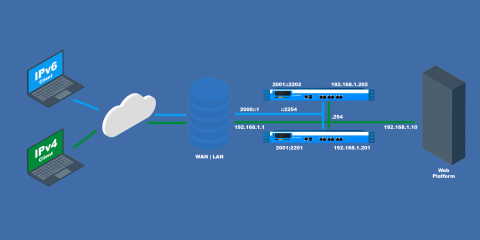
In this blog post, we show how to configure HAProxy Aloha to use it as an IPv6 to IPv4 gateway without modifying anything on your current platform.