For 25 years, HAProxy has been at the heart of application delivery, earning its reputation for legendary performance and reliability. But as applications have evolved into complex, distributed systems, the threats against them have grown exponentially. Today's services face a barrage of sophisticated attacks from AI-powered bots, automated agents, and novel protocol exploits. A load balancer's role is not just about speed; it's about survival.
In this keynote session from HAProxyConf 2025, product leaders Baptiste Assmann and Andjelko Iharos explore how HAProxy has evolved into a critical first line of defense for the modern web. They detail the synergy between the powerful HAProxy data plane and the intelligent HAProxy Fusion control plane, showing how this unified platform provides both blistering performance and multi-layered, next-generation security.
Join them to discover the core principles of HAProxy's design, dive into its advanced security features, and learn how to manage and orchestrate these capabilities at scale across any environment.
Slide Deck
Here you can view the slides used in this presentation if you’d like a quick overview of what was shown during the talk.
Baptiste Assmann
Thank you, guys. Thank you, Dylan, for the introduction. So this is Angelico, and I'm Baptiste.
HAProxy is now 25 years old. The application landscape has changed drastically during that time, evolving from HTTP to APIs. As applications have changed, so have the threats against them.

Today’s threats are more sophisticated and powerful. Attackers use tools like AI, machine learning, bots, and automation. Their goal is to take down your applications, steal data, or disrupt your services.
It is essential to have a layer of defense for any application exposed to the internet. HAProxy and HAProxy Enterprise play a critical role in this, which we will explore in this session.

Andjelko Iharos
Since spring 2023, we have explained the value of our platform, HAProxy One, with three words: simple, scalable, and secure. These values guide our approach as we adapt and respond to the evolving threat landscape.
We have identified that our users need an application delivery and security platform capable of stopping complex and expensive attacks. At the same time, the platform must support your ability to deliver cost-efficient innovation without interrupting your primary business focus.
To achieve this, the platform must be approachable and simple to use. Performance is one of our core tenets, but not at the expense of privacy. Throughout our development, we have remained committed to keeping your data yours and respecting your privacy concerns.
Baptiste Assmann
Today, we will cover the synergy between HAProxy as the data plane and Fusion as the control plane. This unification allows us to provide application delivery and security in a single, integrated platform.
Andjelko Iharos
This approach is unique because we are the only vendor on the market with complete expertise across the entire stack.

We consider this synergy to be the modern security platform. It represents the unification of application delivery and security and is the logical evolution of the HAProxy capabilities we have built over the years.
Our process begins with a global delivery network that we use to gather threat intelligence. Then, through the orchestration capabilities of the Fusion control plane, we deliver these updated security rules and intelligence to fleets of load balancers and HAProxy security modules.

Baptiste Assmann
To start, let's focus on the data plane. As the first point of contact for clients accessing your application or infrastructure, HAProxy is strategically important. This layer must be both reliable and performant.
Because it is the first device clients connect to, the data plane is also the ideal layer to implement your security.
Let's begin with HAProxy Open Source. For 25 years, its development has been built on five core components:
Reliability. Our research and development efforts are focused on making HAProxy exceptionally stable. When people think of HAProxy, the first word that often comes to mind is "reliability."
Performance. High performance is another essential pillar of our platform.
Observability. HAProxy can collect and expose many metrics through various methods, giving you deep insight into your traffic.
Flexibility. We know that every organization has different use cases and application types. The configuration is designed to be highly flexible to accommodate specific rules and traffic management needs.
Security. Finally, security is a critical component and a primary focus of our discussion today.
I also want to make a quick point about contributions. The strength of HAProxy also comes from its open-source community. Many people may hesitate to contribute because they believe it requires writing complex C code. However, a contribution is any action that helps the community and improves the product for everyone.
There are many ways to contribute beyond submitting code:
Writing blog articles or tutorials.
Providing feedback on new features.
Testing the latest builds and reporting bugs.
Speaking at conferences and meetups.
Any action that supports the open-source product is a valuable contribution, and I would encourage you to find ways to do so. Feel free to reach out on Discord if you want some guidance.

This is how I often explain HAProxy to people who don't really know IT and computing. HAProxy acts as the keystone of your infrastructure. If this component is weak, the entire structure is weak. You can have the best developers building the fastest application, but if the load balancer in front of it does not operate correctly, the entire system will fail.
This strategic position in front of your application provides a key advantage, allowing HAProxy to report detailed metrics and insights on all incoming traffic. We are going to see that later when we talk about observability.
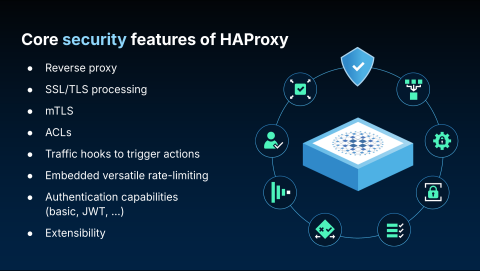
To understand its role in security, let's revisit a few fundamentals. HAProxy is a reverse proxy that runs in the user space. One of its most valued features is SSL/TLS processing. According to “Is TLS Fast Yet?”, HAProxy has a best-in-class TLS stack for handling client-to-server connections. This same high-performance implementation also applies when HAProxy acts as a client, securing its connections to your backend services. This capability extends to mTLS (mutual TLS), and the platform’s configuration offers deep flexibility, allowing you to enforce mTLS based on specific criteria like the SNI (Server Name Indication) or URL.
This flexibility also applies to general traffic management. HAProxy provides traffic hooks that allow you to execute rules at the TCP, HTTP, or SSL level. Developers appreciate these hooks because they can easily implement logic at the reverse proxy layer. This helps manage application changes, such as creating redirects or blocking specific requests, without modifying the application code itself.
Beyond its built-in features, the platform is designed to be highly extensible, and you don’t need to be a C programmer to add custom functionality.
One method is to use the Lua scripting language to extend core features like ACLs and actions. This allows you to create custom converters, fetches, and services directly within HAProxy.
HAProxy's lead architect, Willy, created a Tetris game that runs in your terminal to demonstrate this capability. The game is a powerful example of Lua's interactivity. Instead of a script simply processing a request in the background, this allows a client to interact with it directly and statefully. You can play the game in real time, with HAProxy serving live updates to your terminal in response to your input.
Another method is the SPOE (Stream Processing Offload Engine). SPOE lets you offload custom logic to an external service written in nearly any language, such as Go, .NET, or Java. The key advantage is that your code runs outside the proxy, enabling it to be scaled independently. This is a powerful method for handling complex tasks like custom authentication.
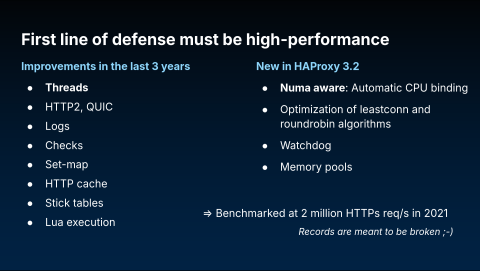
As the first line of defense, HAProxy must be both reliable and high-performance. Performance isn't a destination but a continuous journey for us. With every release, we are committed to improving any component we can. Let's focus on a few significant recent advancements in this area.
First, the threading model in HAProxy has evolved to be nearly lock-free. This simple, thread-safe design scales very well with the available CPU cores. However, performance can be impacted by a machine's NUMA (Non-Uniform Memory Access) configuration. If threads are scaled improperly across different CPU nodes, it can lead to cache misses and performance-degrading context switches.
To address this, recent versions of HAProxy include built-in NUMA discovery. The software automatically creates thread groups and maps them to the correct CPU cores, ensuring you get the best possible performance regardless of the underlying hardware architecture.
To put our performance in perspective, in 2021 we benchmarked HAProxy on an AWS Graviton processor, achieving two million HTTPS requests per second with keep-alive connections. That benchmark was performed before NUMA awareness and other recent threading improvements were introduced. We plan to run new benchmarks soon and expect to break that record.

While performance is a core tenet, security is equally important. We have added several new security features, but I want to focus on how we handle protocol "glitches" in HTTP/2 and HTTP/3.
Recently, attack methods like the HTTP/2 Rapid Reset and Continuation Flood have emerged. These attacks exploit legitimate protocol features, allowing a client to send an excessive number of frames (like RST_STREAM frames) to a server. While technically allowed by the protocol, this behavior can overwhelm and crash some backend servers. New variations of these protocol-level attacks are continually being discovered.
When implementing HTTP/2 and HTTP/3, our engineers noted that the RFCs are ambiguous about handling an excessive number of unusual but technically valid frames. Our solution was to implement a feature that identifies and mitigates these "glitches."
This approach is similar to how HAProxy handles a Slow Loris attack in HTTP/1. The protocol allows a client to send a request very slowly, but this behavior is abnormal and can exhaust server resources. The "glitches" feature applies the same logic to modern protocols.
If a client sends thousands of reset frames when there is nothing to reset, HAProxy identifies this as abnormal behavior and can terminate the connection, protecting the backend servers. This feature has been battle-tested and proven effective by large-scale websites.
A few other recent additions are also worth noting. One is HTTP Reverse Connect, a significant new feature that will be covered in detail in its own session. Another important update is the CRT store, which acts as a centralized catalog for TLS certificates.
Previously, a user with hundreds of frontends using the same certificate had to load it into memory each time. Now, you can load the certificate once into the CRT store and reference it from multiple frontends, greatly simplifying management and saving memory.

In recent versions of HAProxy, we have introduced support for a new SSL library. This multi-year project was motivated by changes in OpenSSL that drastically impacted performance. After evaluating many alternatives, our R&D team selected AWS-LC, an SSL library provided by AWS.
AWS-LC offers several advantages. It provides a FIPS-compliant version and has a five-year maintenance cycle, which aligns perfectly with the lifecycle of HAProxy's stable community releases. The main challenge is that AWS-LC is not packaged in standard operating system repositories like Ubuntu or Red Hat. To solve this, HAProxy Technologies is now building and distributing our own community edition packages and Docker images. These official builds are compiled with AWS-LC to ensure you can easily get the best performance from your installation.
Finally, HAProxy 3.2 introduces support for the ACME protocol to automate certificate management. The HTTP-01 challenge is handled directly by HAProxy itself. For the DNS-01 challenge, which is required for wildcard certificates, HAProxy works with the Dataplane API. The Dataplane API handles the DNS validation, allowing for fully automated certificate issuance and renewal.
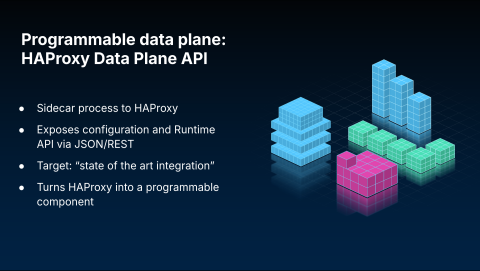
The Dataplane API is a sidecar process designed to make HAProxy fully programmable. It manages the configuration file and runtime operations, exposing a modern RESTful API for control. This allows you to manage HAProxy programmatically using standard tools like curl.
The API also includes helpful features, such as the ability to expose the current configuration in JSON or YAML formats.

In summary, HAProxy delivers both high-performance application delivery and robust security. While its performance is well-known, its powerful security features are just as integral to its design. This commitment to both speed and safety is in the fundamental DNA of the product, our R&D process, and our mission at HAProxy Technologies.
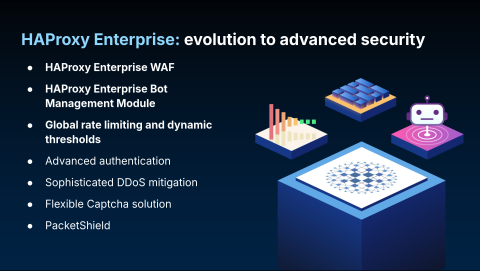
Effective security requires more than just ACLs and basic reverse proxying; it requires deep traffic inspection. For these advanced requirements, HAProxy Enterprise provides a suite of solutions to strengthen your security posture.
This suite includes several key modules:
A Web Application Firewall (WAF) to protect against common exploits.
Advanced Bot Management to identify and mitigate automated threats.
Modules for rate limiting at scale. While the community edition offers effective rate limiting, HAProxy Enterprise provides solutions designed for large, scaled-out environments.
These modules integrate directly with HAProxy's native configuration language. This allows you to create sophisticated policies by combining data from multiple sources. For example, you could create a rule that allows a request that triggers a WAF violation, but only if the client is verified as not a bot and originates from a trusted country.
This approach gives you the full power and flexibility of the HAProxy engine when defining your security policies.

The role of HAProxy Enterprise is to unify native application delivery—such as load balancing and reverse proxying—with next-generation security.
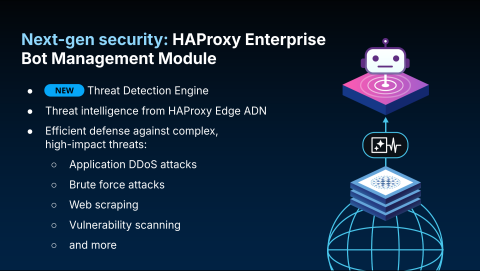
A major focus for us is our Bot Management solution. We recently introduced a key evolution within this module called the Threat Detection Engine. While the module previously focused on IP reputation, the new engine analyzes live traffic to detect behavioral anomalies. It identifies when a client's behavior deviates from the norm, allowing you to create policies for handling suspicious traffic.
Since performance is in our DNA, we designed this protection to be highly resource-efficient. Enabling Bot Management will not degrade the performance of HAProxy or require you to add significant server capacity, which helps control costs.
Our definition of performance is about more than just throughput; it's about maintaining the lowest possible latency. High throughput is meaningless if individual requests are slow. HAProxy is engineered for low latency, and we apply this same rigorous principle to all security components in HAProxy Enterprise.
We operate our own ADN (Application Delivery Network) to enhance our security intelligence. We are the first and largest user of our own solution, which gives us deep expertise in tuning and operating it at scale. This network also provides the traffic data we use to train our machine learning models, but we do so while maintaining our strict commitment to customer data privacy.
This process produces proprietary threat intelligence databases—identifying malicious IPs and client fingerprints—that you can leverage directly in your HAProxy configuration.

The purpose of the new Threat Detection Engine is not to make decisions for you, but to provide rich context by applying labels to traffic. As requests pass through HAProxy, the engine assigns labels that you can use to build powerful security logic.
For example, the engine can identify:
A known good bot, such as a Google crawler.
An AI scraper. Some users may choose to block these requests to protect their data, while others might allow them to ensure LLM training models index their content.
A suspected attack, such as traffic that appears to be part of an application-layer DDoS or a brute-force attempt.
You can then leverage these labels within your HAProxy configuration to create the appropriate policy for each case.
This engine was designed around three core principles. First, it is highly accurate, as it is built and trained using data from our own large-scale traffic.
Second, it is dynamically adaptable. Instead of forcing users to guess static thresholds for brute-force protection, the system intelligently adapts to traffic patterns, making it both more effective and easier to configure.
Finally, it operates with extreme performance efficiency, ensuring that this advanced layer of security does not come at the cost of speed.
Next in the security suite is our Web Application Firewall (WAF), which runs directly within the HAProxy process. We use machine learning to train its default rule set to achieve the best possible "balanced accuracy." This means maximizing the detection of true positives while minimizing false positives, so you don't have to create widespread exceptions for legitimate traffic.
We understand that some organizations require specific rule sets, like the OWASP Top 10, for compliance. While ModSecurity is a common solution for this, it is not known for high performance. To meet this need without compromising on speed, we provide an integration with the Core Rule Set (CRS) for ModSecurity.
The primary advantage of our approach is that you don't need to send every request to the slower ModSecurity engine. Instead, you can use the labels generated by our native WAF and Bot Management modules to invoke ModSecurity only selectively when traffic is deemed suspicious. This intelligent routing significantly reduces performance overhead while still generating the detailed reports required for compliance. The speed and low latency of our native WAF will also be covered in an upcoming session by our customer, Roblox.

Finally, our Edge product is the Application Delivery Network (ADN). Like other global CDNs, our ADN distributes your traffic across a network of edge locations. It inspects and cleans traffic at the edge before forwarding it securely to your origin servers.
This fully managed service also serves a critical internal purpose. As we've mentioned, the vast amount of traffic we process is used to generate our proprietary threat intelligence databases. This intelligence is then fed back into our on-premise security modules, giving every user access to up-to-the-minute, globally-sourced protection.

HAProxy has great power, but great power requires great management.
Andjelko Iharos
Thank you, Baptiste.
So, how do you manage all of these powerful security modules and HAProxy capabilities? The Dataplane API is a very effective tool for a single HAProxy instance or a small cluster.
However, the challenge arises when scaling to tens or hundreds of load balancers. Organizations must manage multiple departments with different requirements, operational needs, and user permission levels. This is where a secure and scalable control plane becomes essential.
While HAProxy provides the foundational security and performance, the control plane is what allows you to harness and orchestrate those capabilities across entire fleets of load balancers.
We built the control plane, HAProxy Fusion, with a clear goal: to simplify the deployment of these powerful features. It enables you to utilize the full benefits of HAProxy more efficiently and effectively across your entire infrastructure.

The Fusion Control Plane is the logical next step, building upon the powerful security and performance features of the HAProxy data plane.
Our security platform is tailored to the needs of enterprise users by centralizing security policy management. It provides a single place to manage configurations across different environments and load balancer clusters. To simplify this process, you can create Security Profiles to customize and bundle the various security features.
These profiles are then applied through a Threat Response Matrix. This matrix allows you to define how your clusters respond to different threats, using the rich information and labels provided by the HAProxy modules. Ultimately, it gives you the flexibility to make the final policy decision based on the insights the platform provides.
The threat intelligence gathered from our global network continuously enhances these capabilities in our enterprise modules.
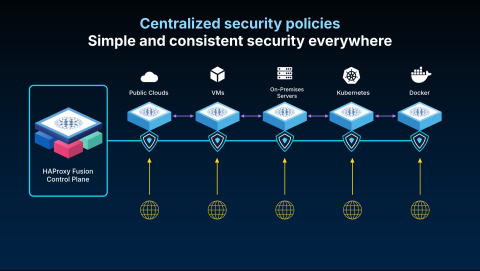
This unification extends to providing consistent management across all your different environments. We can adapt deployments to any infrastructure, including on-premise data centers, public clouds like AWS and Azure, private clouds, and Kubernetes. All of these diverse environments can be managed and controlled through the same central control plane, ensuring you can apply consistent workflows across your entire organization.
Kubernetes and containers are treated as first-class citizens in the Fusion Control Plane. Our integration goes beyond acting as just an external load balancer; we also provide service discovery directly from your Kubernetes deployments. This allows you to grant application developers a degree of control over their service's load balancing using familiar tools like kubectl.

This flexibility means we are not limited to managing traditional north-south (client-to-server) traffic. We also excel at managing east-west (server-to-server) traffic, a less commonly known but powerful capability. By combining service discovery with native HAProxy features like advanced routing and map files, we provide the building blocks for any internal load balancing scenario.
This is especially useful for complex architectures such as multi-cloud, hybrid-cloud, or multi-Kubernetes cluster deployments. In all these scenarios, HAProxy Fusion provides a single point of control and a single source of truth for managing and securing your application delivery infrastructure, regardless of its location.
To summarize, we support the full range of deployment environments:
Bare Metal: For achieving the absolute best HAProxy performance and lowest latency.
Private and Public Clouds: With enterprise images available directly from marketplaces like AWS.
Containerized Environments: With full support for Docker images, making deployment in Kubernetes and other container platforms seamless.
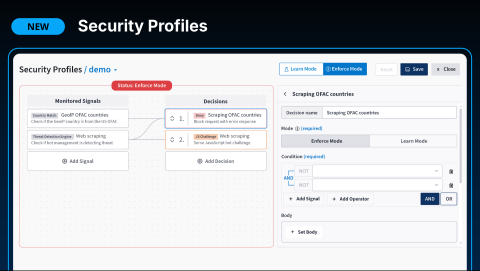
A major new feature in the upcoming HAProxy Fusion release is Security Profiles. These profiles are designed to simplify using the many security capabilities built into HAProxy. This includes not only dedicated security modules but also powerful general-purpose features like ACLs, routing rules, and backend switching, which can be combined to create a strong security posture.
While you can already configure these features manually or via API, that approach offers maximum flexibility at the cost of a steep learning curve. Security Profiles change this by providing a logical arrangement of security capabilities, rather than a direct one-to-one mapping of HAProxy configuration directives.
This allows you to focus on what you want to accomplish—your security outcome—rather than the complex internal details of implementing it with the right combination of ACLs, map files, and variables. You retain the flexibility to customize settings within a more guided and logical framework that includes sensible defaults.
For instance, implementing GeoIP blocking manually requires loading the correct module, configuring ACLs to inspect requests, setting variables, and then acting on them. With Security Profiles, these steps are combined into a straightforward, visual interface.
This allows you to easily build security policies tailor-made for specific applications, departments, or environments.
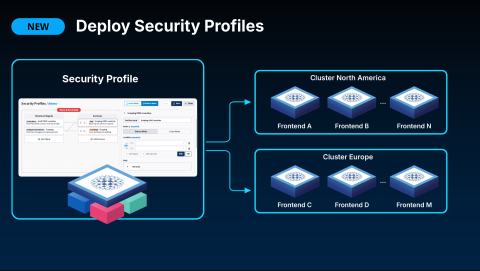
When deploying Security Profiles, you are not limited to a single, global configuration. Instead, you can create multiple profiles and apply them selectively to specific load balancer clusters or individual frontends. This approach gives you the power of templating.
You can design different profiles for different application groups—for example, a strict profile for a public-facing API and a more lenient one for an internal service. These can be mixed and matched as needed, even within a single HAProxy cluster, while Fusion remains your single point of control.
Crucially, every action available in the HAProxy Fusion UI is also exposed through the API. This provides flexible workflow options. You can visually build a profile in the UI and then use the API to apply it programmatically as part of your CI/CD pipeline. Alternatively, the entire process can be fully automated via the API, from creating profiles to applying them.

The Threat Response Matrix is where Security Profiles come to life. It is a powerful interface where you map the signals gathered by HAProxy to specific actions. These signals can come from various sources, such as our Threat Detection Engine, GeoIP data, custom request headers, or labels from the WAF. This matrix puts the power in your hands, providing the tools and intelligence you need to make the final policy decisions easily and effectively.
Based on the incoming signals, you can trigger a wide range of responses, including:
Tarpitting the connection to slow down a suspicious client.
Issuing a JavaScript challenge or CAPTCHA to verify a user.
Changing the request's routing to a different backend, such as a honeypot.
Explicitly allowing or denying the traffic.
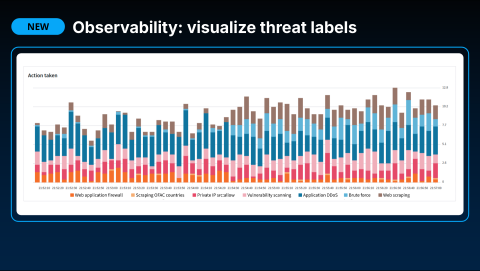
Applying a Security Profile also provides deeper visibility into your traffic. You can see precisely how profiles label your requests and influence your application delivery. HAProxy Fusion achieves this by centrally collecting the access logs from all your load balancers. These logs are enriched with detailed information from all the security modules and the signals you've configured.
HAProxy Fusion then synthesizes this data into intuitive dashboards and visualizations, giving you the tools to instantly understand what is happening with your traffic and how your security policies are performing. As with all our features, this visibility is also fully available through the API, allowing you to integrate this data into other systems.
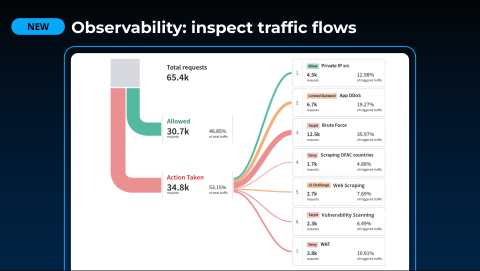
This observability and insight are delivered in real-time, so you do not have to wait for reports to be generated after the fact. This allows you to see the immediate effect of your applied Security Profiles on active traffic and on any particular frontend.
We provide a detailed breakdown of traffic responses, so you can instantly validate the impact of any change you make to a Security Profile or load balancer configuration.

We have discussed creating Security Profiles and configuring advanced security policies. But how do you deploy and manage these configurations across tens, hundreds, or even thousands of load balancers?
Even with the simplification that profiles provide over editing raw HAProxy configuration files, managing deployment at scale introduces a new set of challenges that must be addressed.
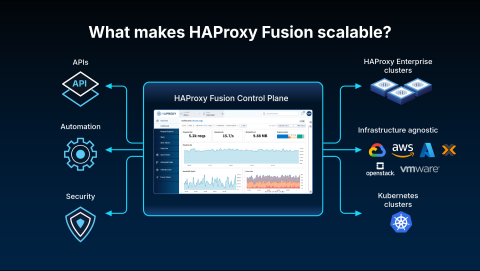
For the large environments that many of our users operate, the Fusion Control Plane provides critical orchestration capabilities. Its primary purpose is to orchestrate configuration changes across your entire infrastructure, acting as a single point of access where you can manage all your load balancers, clusters, and logical groupings through a unified API.
This allows your automation and CI/CD pipelines to interact directly with the Fusion API. Through the API, you can retrieve the status of your load balancers, verify which security policies are applied, and confirm the results of any configuration change.

The HAProxy Fusion API is built on the OpenAPI specification, making it incredibly straightforward. This allows you to leverage a wide range of off-the-shelf tools for interaction or easily build custom client libraries for deep, programmatic control of your infrastructure.
A control plane for hundreds of load balancers would have limited utility if it weren't highly available. Therefore, HAProxy Fusion was built from the ground up to ensure resiliency against hardware and service failures. This is why the default deployment for HAProxy Fusion is a three-host cluster, ensuring it remains a reliable single source of truth.
The Security Control Plane is just one of many simplified workflows in HAProxy Fusion. We are committed to adding more of these guided workflows and exposing HAProxy capabilities in a way that naturally fits how our users work.
A key example of this is Service Discovery, which automates tracking infrastructure changes. Managing configurations at scale isn't truly useful if you must manually write extensive glue scripts to keep your load balancers updated.
Our Service Discovery feature solves this problem. It currently supports Kubernetes and Consul, with more providers on the way. You can configure HAProxy Fusion once to listen for changes—such as new services in a Kubernetes namespace—and the process is fully automated from that point on.
When a change is detected, HAProxy Fusion automatically regenerates the relevant parts of the HAProxy configuration, runs stringent validation checks, and pushes the new configuration to the appropriate load balancers.
This automation closes the loop for today's dynamic environments. Our largest users are pushing their limits with thousands of backend servers, driving us to optimize for speed and scalability in the control plane itself, not just the data plane.
This reflects our core design philosophy for HAProxy Fusion: an API-first platform, built for high availability, and constantly evolving with automated workflows to keep up with dynamic infrastructure.
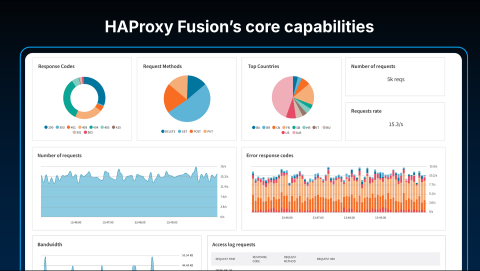
Once you have configured your Security Profiles, enabled Service Discovery, and automated the delivery of HAProxy configurations to your load balancers, the natural next question is: "What is the effect of these changes on my live traffic?"
This is where observability, another of our core capabilities, comes into play. HAProxy Fusion includes a suite of out-of-the-box visualizations and a powerful report editor. This allows you to create custom reports that are automatically populated with live, real-time data as it comes in from your fleet, giving you immediate insight into the performance and security of your applications.

We also provide the Request Explorer, a tool that allows you to observe individual requests in real-time. You can inspect every detail associated with a request, including applied security labels, SSL versions, and processing latencies. This creates a "single pane of glass," providing visibility as deep as you need into everything happening with your application traffic.
HAProxy Fusion also ensures that all configuration changes are deployed consistently and checked for validity. By default, it enforces that all load balancers in a cluster have the exact same configuration, preventing out-of-sync issues.
This eliminates scenarios where some load balancers might reject traffic due to new security settings, while others do not. This situation cannot happen when using the Fusion Control Plane.
Finally, scalability is built into all of these features. Fusion allows you to organize clusters into logical groups, which simplifies the management of different environments. This makes it easy to segment your infrastructure, whether you are splitting it by geographical region, application type, or deployment stage, like production and staging.

This summarizes our mission for HAProxy Fusion: continuously building upon this platform, streamlining critical workflows to make them easier to manage, and empowering you to secure your entire enterprise environment.
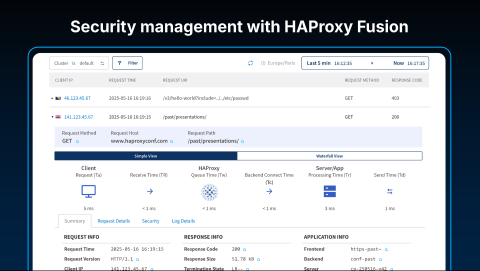
The Request Explorer is a powerful tool for deep, individual request visibility. The detailed information it provides is gathered through a turnkey process built directly into the data plane and the HAProxy Fusion Control Plane.
These observability features are part of the base functionality of the Fusion Control Plane. The new Security Control Plane capabilities are designed to integrate seamlessly with this existing foundation, extending its power naturally and intuitively.
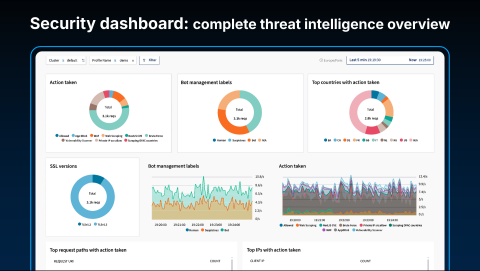
This creates a seamless workflow. You can begin by observing high-level traffic patterns on the main dashboard. If an anomaly catches your eye, you can drill down into the Request Explorer for detailed, request-level inspection.
Should you discover a threat, you can immediately pivot to the Security Control Plane to define a new signal and map it to a specific response, closing the security loop in real-time.
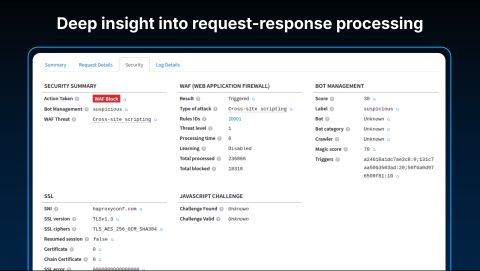
Once you define a response and apply it to a cluster or front end, the change is deployed in parallel across all relevant load balancers with minimal traffic disruption. This is achieved using advanced techniques, such as making in-memory changes through the HAProxy runtime API, a process facilitated by the local data plane agent.
This seamless deployment workflow is not limited to just HAProxy configuration changes. It applies equally to updating WAF rules, renewing TLS certificates, distributing bot management signatures, or deploying any other necessary files to your load balancers.

Finally, we want to highlight our management of TLS certificates. As mentioned earlier, support for the ACME protocol, pioneered by Let's Encrypt, is integrated directly into HAProxy Fusion. This enables a more performant and scalable approach to certificate renewals across your fleet.
Instead of each individual load balancer attempting to complete its own ACME challenge—a process that does not scale well across hundreds of instances—Fusion centralizes this function for the entire fleet.
While the amount of available data is vast, our observability tools are fully customizable. You have the ability to filter what is shown and to generate your own visualizations and reports, ensuring you see exactly the information that is most relevant to you.

So, what's coming next, Baptiste?
Baptiste Assmann
Thanks, Andjelko.
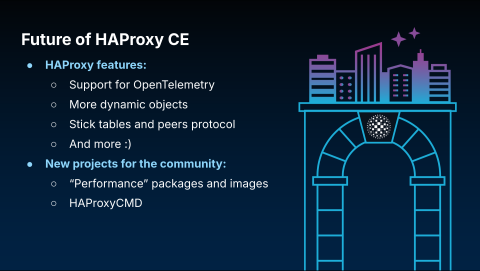
Looking ahead, we have several exciting plans for the HAProxy community edition.
First, we plan to add native support for OpenTelemetry. This will replace our previous support for OpenTracing, which is no longer an active project, and will provide a modern, comprehensive observability framework.
We also plan to expand support for dynamic objects at runtime, a common request from the community. Currently, many components—such as server entries, the SSL/TLS stack, map files, and ACLs—can already be changed live without a reload. Our goal is to extend this powerful capability to even more objects.
A major rework of stick tables and the peers protocol is also on the roadmap. This effort will focus on increasing performance and expanding support for more features and use cases. We are actively seeking feedback from users of these features, so if you would like to influence the future direction of this work, please contact us.
Finally, we plan to release two new projects for the community:
Performance Packages: As mentioned previously, these will be official packages of HAProxy compiled with AWS-LC for optimal performance, available for popular distributions like Debian and Ubuntu.
HAProxyCMD: This new command-line tool is designed to simplify common operational tasks. It will provide a single, intuitive interface for actions like installing, upgrading, and querying HAProxy, eliminating the need for users to learn multiple underlying tools like socat. Looking further ahead, we are exploring the possibility of integrating AI to allow for natural language interaction with this tool.
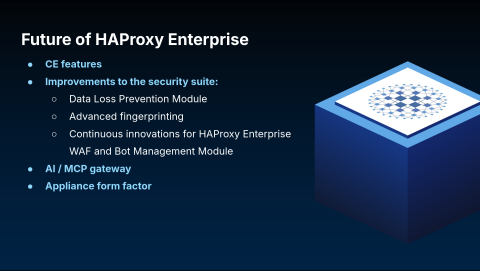
Our roadmap for HAProxy Enterprise begins with inheriting all the improvements from the community edition, including the planned support for OpenTelemetry. We will also continuously enhance our security suite with several key additions:
Data Loss Prevention (DLP): A new, dedicated module for Data Loss Prevention (DLP). While some of this is possible today, this will be a much more focused and powerful solution to address this common request.
Advanced Fingerprinting: Significant advancements in client fingerprinting to provide more accurate signals for building security policies in HAProxy Fusion.
WAF and Bot Management: Continued innovation and improvements for our WAF and Bot Management modules.
We will also introduce an AI gateway solution in the near future. The goal is to place HAProxy in front of AI application servers to protect the underlying APIs that power them.
As user requests to AI services like Gemini are translated into API calls, HAProxy will provide a critical security layer, just as it does for traditional web applications. We will build out dedicated features to secure these emerging AI-driven architectures.
Finally, we plan to offer HAProxy Enterprise in a virtual appliance form factor to provide our customers with another simple and turnkey deployment model.

Andjelko Iharos
The roadmap for the Fusion Control Plane also includes significant updates. A key addition will be support for the official Kubernetes Gateway API. This involves integrating our new unified HAProxy Kubernetes Ingress Controller with HAProxy Fusion and further expanding its service discovery capabilities.
We also plan to bring more AI-powered intelligence to the platform to enable predictive security analysis. This intelligence will also allow Fusion to make smarter, localized security decisions based on your specific traffic patterns, without needing to wait for external threat intelligence updates.

As application developers increasingly build AI-powered services, we want to stay ahead of the curve. Our goal is to provide infrastructure teams with the tools to secure these new application architectures, ensuring they can maintain full security control without interrupting innovation.
Looking even further ahead, we are exploring using this same technology to enhance the Fusion user experience itself. The vision is to train a Large Language Model (LLM) on our own documentation and platform specifics. This would provide users with an interactive assistant, capable of offering insights and guidance on how to best interact with the Fusion platform.

We are building Terraform modules and building more higher-level workflows. We're also excited to centralize the management of troubleshooting tools through the HAProxy Fusion control plane, allowing you to do more troubleshooting without having to log into your load balancers.
We have a lot to do and work on, but for now, that's where we're going to wrap up for today.
Baptiste Assmann
Yes, and we have some demonstrations where you can see all this in action. Thank you, everyone.



















































