CAPTCHA (completed automated public Turing test to tell computers and humans apart) is an automated mechanism websites use to determine whether a user is a human or a bot. The CAPTCHA's goal is to block automated (and often malicious) bots from accessing services — and subsequently orchestrating DoS or DDoS attacks. Any spam might otherwise consume crucial backend resources that services need to run effectively.
Websites will typically display a CAPTCHA during authentication, such as when logging into an online account or submitting a web form (to name just two examples). However, websites can lock certain actions behind a CAPTCHA for any compatible services for which abuse causes slowdowns or downtime.
CAPTCHA takes philosophical cues from the originator of the Turing test, Alan Turing. This pioneering test measures a machine's ability to emulate or achieve human-level intelligence. CAPTCHA builds on this by presenting a task that only a real person behind the keyboard should be able to complete. It gatekeeps other actions on the site that users commonly take.
While CAPTCHA was first developed in the late 1990s and shortly after, the term "CAPTCHA" didn't enter common usage until 2003. Researchers at Carnegie Mellon University coined the term and set the precedent for what would become one the internet's fundamental security measures.
How do CAPTCHAs work?
CAPTCHA tests are thus designed to be relatively simple for humans to solve, but not bots. In their basic form, they typically require a user to type letters that are displayed in a box rendered on-screen.
This text is obfuscated so that it's more difficult for OCR software to read (and while LLMs are usually able to read them as well as humans, they're also too expensive for most bots). This is the traditional version of CAPTCHA with the fewest steps and complexity. However, it has evolved over time to better thwart OCR tools with increased sophistication.
Many modern CAPTCHA boxes also work in the background to validate each user's interaction with the page, and use client fingerprinting techniques to detect bots capable of deciphering those letters.

When an entity — whether a human user or automated bot — successfully completes the CAPTCHA, the service assumes that they're indeed human. When the test taker fails, they're prompted to submit another answer after interpreting a new set of random characters, which are often distorted in a different way than before.
Some sites present a seemingly endless stream of solvable CAPTCHAs when a user fails the test. Others may instead give the client a limited number of attempts before blocking access. Alternatively, they may present a different type of test entirely to give the user a fair attempt without reducing security.
The evolution of CAPTCHA
Modern variants of older CAPTCHA tests, such as Google's reCAPTCHA, that use puzzle-solving tasks to verify humanity. First created by scientist Luis von Ahn in 2007 and absorbed by Google in 2009, reCAPTCHA asks users to identify photos (or portions of them) or physically pull digital puzzle pieces into gaps to form a complete image. Technically speaking, it's a product as well as a solution.
There are also a number of competitors to Google’s reCAPTCHA such as hCaptcha, Friendly Captcha, and Cloudflare Turnstyle which similarly go beyond asking users to simply enter letters.
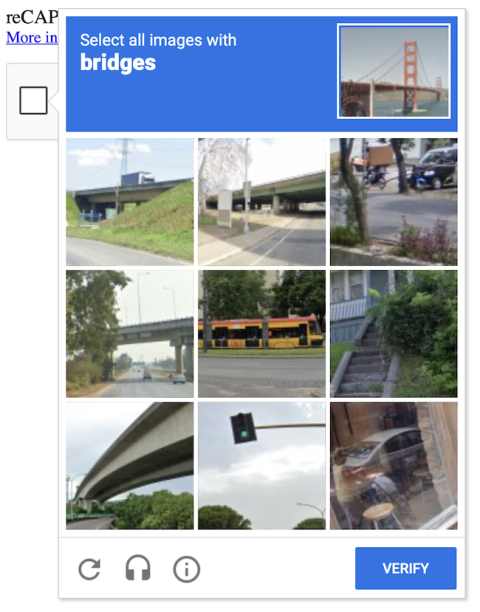
reCAPTCHA tests may also examine cursor inputs to distinguish bots from humans. For example, a human user often drags their cursor along an irregular path while engaging with a reCAPTCHA — while a machine-driven cursor typically takes a neater, more rigid path.
There are multiple difficulty levels to each CAPTCHA and especially reCAPTCHA, ranging from easy to difficult. Harder tests might require more complex pattern recognition and object identification within a given image or set of images. Each successive version of reCAPTCHA, including reCAPTCHA v2 (2014) and reCAPTCHA v3 (2018), has put its own spin on this test to keep things fresh. There are also invisible reCAPTCHAs that silently analyze user behavior and browsing patterns to detect bot activity. The website presents a typical reCAPTCHA grid if a user's status cannot be determined by these means alone.
Not every action requires the utmost security, however. While some reCAPTCHA systems require deeper verification — even presenting users multiple images in a row for added safety — they may also accept a simple check of that "I'm not a robot" box we've become so accustomed to seeing across the web. In any case, any CAPTCHA-based system is not an adequate replacement for any bot detection and blocking measures offered through a more comprehensive security suite.
Then there are hCaptcha tests, which ask users to form associations between a chosen, pictured object and a grid of random objects. For example, the hCaptcha might show a picture of a manual air pump, then ask which objects presented beneath it can be inflated using that same air pump.
CAPTCHAs have continued to evolve over time. Multiple companies (not just Google) offer unique approaches to CAPTCHA verification to keep bot programmers on their toes and differentiate themselves from competing alternatives.
You’ve mastered one topic, but why stop there?
Our blog delivers the expert insights, industry analysis, and helpful tips you need to build resilient, high-performance services.
Does HAProxy offer CAPTCHA support?
Yes! The HAProxy Enterprise CAPTCHA module adds automated CAPTCHA support from numerous providers and solutions, such as reCAPTCHA v2, reCAPTCHA v3, reCAPTCHA Enterprise, hCaptcha, and others. Implementing CAPTCHA-based security is easy with HAProxy Enterprise.
To learn more about evolving CAPTCHA support in HAProxy, check out our HAProxy Enterprise 3.0 announcement and our HAProxy Enterprise 3.1 announcement.