HAProxy Exposes a Prometheus Metrics Endpoint
In this blog, we’ll explain how to set up the metrics endpoint, how to configure Prometheus to scrape it and offer guidance on graphing and alerting the data.

Chad Lavoie is the Director of Support for HAProxy Technologies. Chad specializes in HAProxy configurations for request processing, web scraping/DDoS protection, and some scripting for flavor.
In this blog, we’ll explain how to set up the metrics endpoint, how to configure Prometheus to scrape it and offer guidance on graphing and alerting the data.

HAProxy has best-in-class bot protection capabilities for detecting and defending against many types of unwanted bot traffic. Read on to learn how.

HAProxy's high-performance security capabilities are utilized as a key line of defense by many of the world's top enterprises. Application layer DDoS attacks are aimed at overwhelming an application w

This guide explains the 4 core sections and key directives such as setting the haproxy default timeout, timeout client, and timeout server.

In this post, you’ll learn how to create an HAProxy map file, store it on your system, reference it in your HAProxy configuration, and update it in real time.
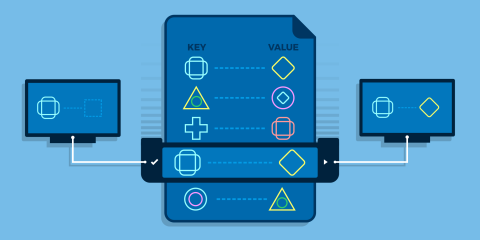
Learn more about HAProxy's fast, in-memory storage called stick tables that let you track user activities, including malicious ones, across requests.

A practical guide to HAProxy ACLs. Learn the syntax and follow step-by-step examples to block traffic, redirect users, choose backends, and enhance security.

Microservices architectures require the ability to make frequent app delivery changes in an automated and reliable way. The HAProxy Runtime API enables this.

Why use the Proxy protocol? Well, when you lose client information like IP address when relaying connections through proxies, this tends to prevent you from...
