Observability
View logs and configure a syslog server
This page applies to:
- HAProxy ALOHA - all versions
HAProxy ALOHA does not permanently store logs. It stores them only in memory and not on the filesystem, making them available for viewing for a limited amount of time via the Logs tab. For long-term storage of logs, deploy a remote syslog server and configure HAProxy ALOHA to ship logs to it.
- Select the Logs tab to view a limited history of system, load balancer, administrative, and general traffic events.
- You can also log the traffic that traverses a specific HAProxy ALOHA VIP.
Concepts Jump to heading
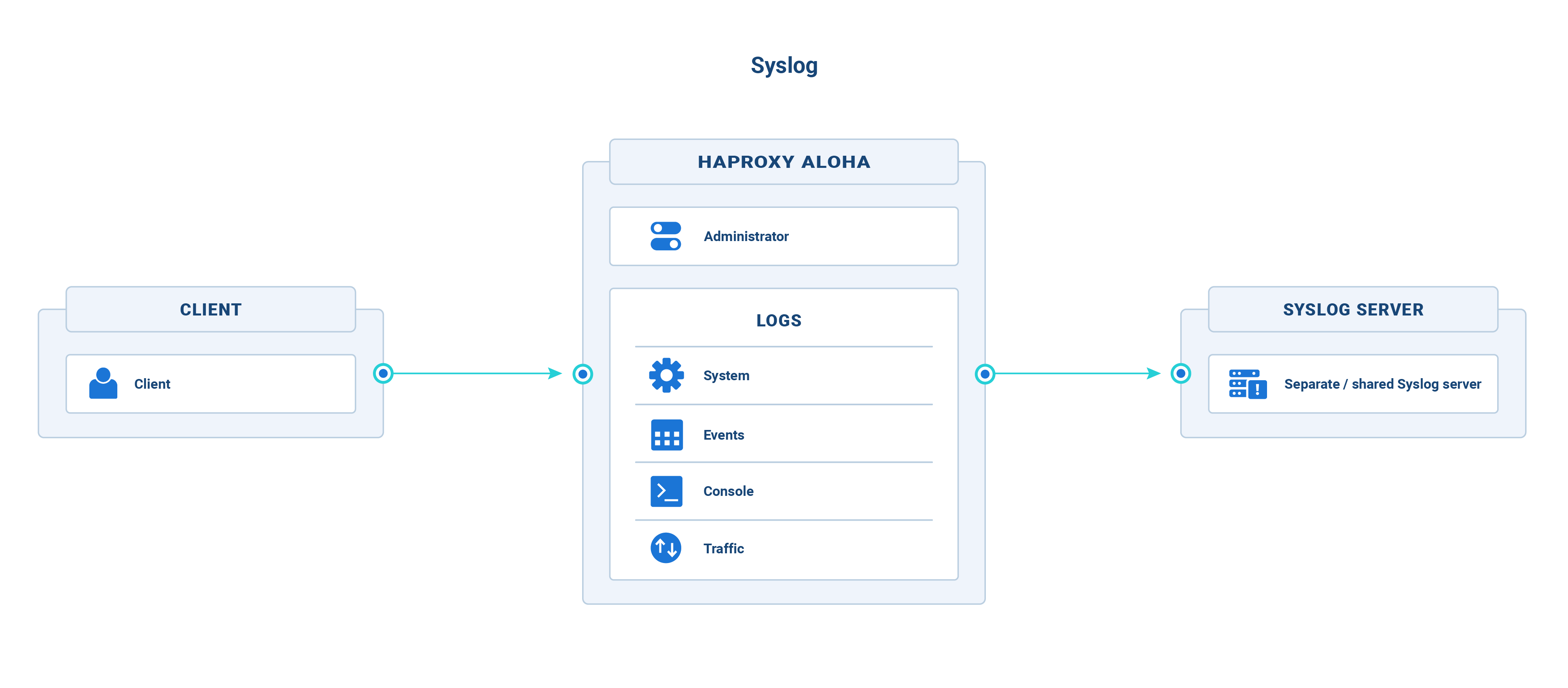
HAProxy ALOHA generates several types of logs, each of which can be collected and sent to a separate or a shared syslog server. The types are defined in the table below, where each has a unique name that you will use to configure it.
| Name | Description |
|---|---|
| console | Administration Web UI events. |
| dataplaneapi | Data Plane API events, requires enabling the Data Plane API. |
| events | Load balancer events. |
| sec-offloader-events | Important Web Application Firewall events at the syslog level of notice and above. This includes processing errors and rule matches. The level is set in /app/security/etc/sec-offloader/global.def. Requires enabling the WAF. |
| sec-offloader-traffic | Web Application Firewall HTTP access logs, requires enabling the WAF. |
| system | Major operating system events. |
| traffic | Traffic traversing all HAProxy ALOHA frontends. |
This diagram illustrates how HAProxy ALOHA generates different types of logs that you can send to a syslog server.
View the Logs tab Jump to heading
To view logs in the HAProxy ALOHA UI:
-
Go to the Logs tab.
From here you can view, filter, and download the recent log messages.
Send logs to a syslog server Jump to heading
In this section, you will learn how to configure HAProxy ALOHA to sends its logs to a syslog server.
Configure the syslog server Jump to heading
Configure a remote syslog server to receive log entries. This server should be an additional Linux server external to your HAProxy ALOHA instance whose firewall and other network settings allow incoming log traffic from your HAProxy ALOHA instance.
On this Linux server:
-
Install a syslog server such as
rsyslog.Example:
nixsudo apt install rsyslognixsudo apt install rsyslog -
Create a file named
/etc/rsyslog.d/10-aloha.confwith the directives below.10-aloha.conftext$ModLoad imudp$UDPServerRun 514$ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormatif $fromhost-ip=='172.16.24.237' then /var/log/aloha.log10-aloha.conftext$ModLoad imudp$UDPServerRun 514$ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormatif $fromhost-ip=='172.16.24.237' then /var/log/aloha.logHere, we configure rsyslog to listen on all IP addresses at port 514 and to store incoming log messages in the file
/var/log/aloha.logwhen they come from the HAProxy ALOHA IP address.The directives are as follows:
Directive Description $ModLoad imudp Receive logs over UDP. $UDPServerRun 514 Start on the specified port. $ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormat Use the traditional syslog format. if $fromhost-ip==‘172.16.24.237’ then /var/log/aloha.log Store incoming log messages in the file /var/log/aloha.logwhen they come from the HAProxy ALOHA IP address. Replace172.16.24.237with your own IP address. You can specify several of these directives, or usestartswithto match a range of IPs. -
Restart the
rsyslogserver.nixsudo systemctl restart rsyslognixsudo systemctl restart rsyslog
Configure HAProxy ALOHA Jump to heading
You can send one or more types of logs to your syslog server, as shown in this section.
Caution
In the cases below, be sure to specify the syslog server’s IP address, not its FQDN. HAProxy ALOHA doesn’t perform DNS resolution for its internal system, which may slow the boot process. If you need to be able to reference the server by name, we advise statically declaring it in the /etc/hosts file. See set static server names and IP addresses in the hosts file for more information.
Send system events Jump to heading
Configure the system log type to send major HAProxy ALOHA operating system events, such as kernel errors, to an external syslog server.
-
From the Services tab, click syslog setup.
-
In the
service syslog systemsection, specify the IP address and port of the destination syslog server. There can be only one server in the section.Example: Send
systemmessages to a syslog server listening at172.16.24.236on UDP port514.rubyservice syslog systemserver 172.16.24.236:514rubyservice syslog systemserver 172.16.24.236:514 -
Restart the syslog service.
The
Message 7010: Last action returns successmessage displays. -
To make the configuration changes persist after a reboot, go to the Setup tab and click Save within the Configuration section.
Send load balancer events Jump to heading
Configure the events log type to send errors related to starting/stopping the haproxy service, and related errors or warnings, to an external syslog server.
-
From the LB Layer7 tab, ensure that the
defaultssection has alog globalline:haproxydefaults unnamed_defaults_1log globalhaproxydefaults unnamed_defaults_1log global -
From the Services tab, click syslog setup.

-
In the
service syslog eventssection, specify the IP address and port of the destination syslog server. There can be only one server in the section.Example: Send
eventsmessages to a syslog server listening at172.16.24.236on UDP port514.rubyservice syslog eventsserver 172.16.24.236:514rubyservice syslog eventsserver 172.16.24.236:514 -
Restart the syslog service.
-
To make the configuration changes persist after a reboot, go to the Setup tab and click Save within the Configuration section.
Send console events Jump to heading
Configure the console log type to send events such as logins to the HAProxy ALOHA command-line interface to an external syslog server.
-
From the Services tab, click syslog setup.

-
In the
service syslog consolesection, specify the IP address and port of the destination syslog server. There can be only one server in the section.Example: Send
consolemessages to a syslog server listening at172.16.24.236on UDP port514.rubyservice syslog consoleserver 172.16.24.236:514rubyservice syslog consoleserver 172.16.24.236:514 -
Restart the syslog service.
-
To make the configuration changes persist after a reboot, go to the Setup tab and click Save within the Configuration section.
Send traffic events for all frontends/backends Jump to heading
Configure the traffic log type to send traffic logs for all frontends to an external syslog server. This configuration logs all load balancer traffic.
-
From the LB Layer7 tab, ensure that the
defaultssection has alog globalline:haproxydefaults unnamed_defaults_1log globalhaproxydefaults unnamed_defaults_1log global -
From the Services tab, click syslog setup.

-
In the
service syslog trafficsection, specify the IP address and port of the destination syslog server. There can be only one server in the section.Example: Send
trafficmessages to a syslog server listening at172.16.24.236on UDP port514.rubyservice syslog trafficserver 172.16.24.236:514rubyservice syslog trafficserver 172.16.24.236:514 -
Restart the syslog service.
-
To make the configuration changes persist after a reboot, go to the Setup tab and click Save within the Configuration section.
Send traffic events for a specific frontend/backend Jump to heading
You can send traffic that traverses a specific HAProxy ALOHA frontend or backend.
-
On the remote rsyslog server, edit the
/etc/rsyslog.d/10-aloha.conffile.Below, we capture messages from syslog facilities
local0and write them to theexample-frontend-traffic.logfile.10-aloha.conftextlocal0.* /var/log/example-frontend-traffic.log10-aloha.conftextlocal0.* /var/log/example-frontend-traffic.log -
On HAProxy ALOHA:
-
Click the LB Layer7 tab.
-
Add the following directive to frontend and backend sections:
textlog <syslog server IP address>:<port> <facility>textlog <syslog server IP address>:<port> <facility>Example: For events occurring on frontend
example-frontendand backendexample-backend, send log messages to an rsyslog server listening at172.16.24.236on UDP port514with facilitylocal0.haproxyfrontend example-frontendbind :80mode httplog 172.16.24.236:514 local0option httplogdefault_backend example-backendbackend example-backendlog 172.16.24.236:514 local0server s1 172.16.24.236.10 checkhaproxyfrontend example-frontendbind :80mode httplog 172.16.24.236:514 local0option httplogdefault_backend example-backendbackend example-backendlog 172.16.24.236:514 local0server s1 172.16.24.236.10 check -
To make the configuration changes persist after a reboot, go to the Setup tab and click Save within the Configuration section.
-
LB Layer7 tab: Conditional logging Jump to heading
Available since
- HAProxy ALOHA 17.0
Using the when() converter, you can configure the load balancer to emit certain log messages only when certain conditions are met, for example, on error or because of another abnormal state. See when() converter for more information.
LB Layer7 tab: log profiles Jump to heading
Available since:
- HAProxy ALOHA 17.0
You can define custom log formats in named log profiles that you can then apply wherever needed.
You can define as many log profiles as you want, giving each a name allowing you to apply it independently. With log profiles, you can choose the one best suited for each log server and even emit logs to multiple servers at the same time, each with its own format. Log profiles also allow you to write log messages when different events occur, such as when accepting a connection, receiving a request, connecting to a backend server, and receiving a response.
Log profiles present plenty of opportunities:
- Create a log profile for emitting timing information to see how long the HAProxy service took to handle a request.
- Create a log profile that emits the maximum amount of data for use in debugging.
- Switch the log format just by changing the
profileargument on thelogline. - Reuse profiles across multiple frontends.
- Decide whether you want to emit messages for every step defined in a profile or for only some of them by setting the
log-stepsdirective.
In the example below, we define two log profiles on the LB Layer7 tab: one named syslog, which uses the syslog format, and another named json, which uses JSON.
haproxy
haproxy
In this example:
- For
syslog, we set the optionallog-tagdirective inside to change the syslog header’stagfield, to give a hint to the syslog server about how to process the message. - The
ondirective sets when to emit the log message. We’re emitting the log message on thecloseevent, when HAProxy has finalized the request-response transaction and has access to all of the data.
Our frontend uses both log profiles. By setting the profile argument on each log line, the frontend will send syslog to one log server and json to another. It’s required to also enable logging in the frontend, which we accomplish by setting option httplog, but option tcplog would also work.
haproxy
haproxy
By default, HAProxy emits a log message when the close event fires, but you can emit messages on other events, too. The supported events are accept, close, connect, error, request, and response.
By tweaking the syslog profile to include more on lines, we have logged a message at each event in HAProxy’s processing:
haproxy
haproxy
To enable these extra messages, set the log-steps directive to all or to a comma-separated list of events:
haproxy
haproxy
Remove existing log global lines or else you’ll get log messages twice, once from the global log line and once from your frontend’s log line.
LB Layer7 tab: do-log action Jump to heading
Available since:
- HAProxy ALOHA 17.0
The do-log action allows you to emit custom log messages at any point in the processing of a request or response. Add the do-log action where desired in your LB Layer7 configuration. In the example below, we set a variable named req.log_msg and then use a do-log action to log the variable value.
haproxy
haproxy
Update your syslog log-profile section (see Log profiles) so that it includes the directive on http-req, which defines the log format to use whenever http-request do-log is called.
The following example log format prints the value of the variable req.log_msg:
haproxy
haproxy
Your log will show the custom log message:
text
text
The do-log action works with other directives, too. Each matches up with a step in the log-profile section:
| Directive | Matches event |
|---|---|
http-request do-log |
http-req |
http-response do-log |
http-res |
http-after-response do-log |
http-after-res |
quic-initial do-log |
quic-init |
tcp-request connection do-log |
tcp-req-conn |
tcp-request session do-log |
tcp-req-sess |
tcp-request content do-log |
tcp-req-cont |
tcp-response content do-log |
tcp-res-cont |
Syslog service reference Jump to heading
The syslog service on the Services tab supports the following configuration directives:
| Directive | Description |
|---|---|
console_level <level> |
Sets the maximum syslog severity level to send to the console. |
forward_timestamp (version 13.5 and 14.0) |
Adds an RFC 3164 header to log messages if it is missing (which includes a timestamp and hostname). The log’s raw message changes from: <134>haproxy[26940]: Connect from 192.168.68.117:60749 to 192.168.68.124:80 (web/TCP)to: <134>Jan 24 16:49:40 ALOHA1 haproxy[26940]: Connect from 192.168.68.117:60749 to 192.168.68.124:80 (web/TCP) |
keyid <key> |
An identifier to use for a second syslog server. |
listen <local IP[:port]> |
Collect UDP log messages from the given local IP address and optional port. |
listen_kernel |
Collect kernel messages. |
[no] listen_unix |
Collect (or do not collect if prefixed with no) messages from /dev/log. |
output "buffer"|<filename> |
Records log messages to either a ring buffer or to a file. |
rotate <number> |
The number of log files to keep before rotating them. |
server <remote IP:port> |
The IP address and port of a remote syslog server that will receive log messages. |
size <kb> |
The maximum size in kilobytes of the buffer or file when output "buffer" or output <filename> is set. |